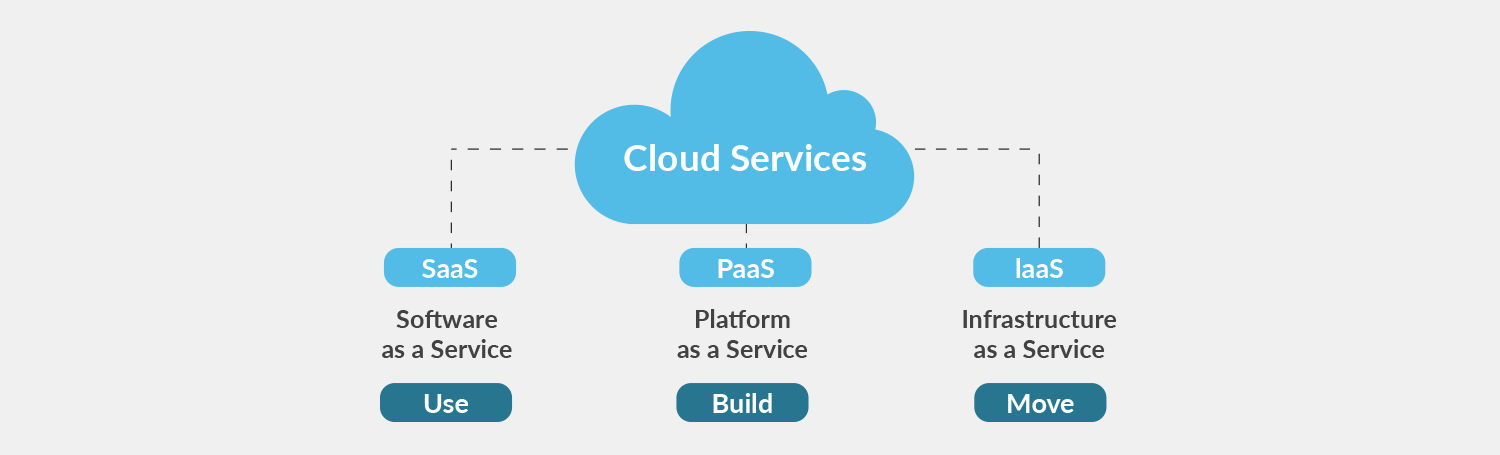
LinkDaddy Cloud Services - Comprehensive Solutions for All Your Requirements
LinkDaddy Cloud Services - Comprehensive Solutions for All Your Requirements
Blog Article
Take Advantage Of Cloud Services for Improved Information Protection
In today's digital landscape, the ever-evolving nature of cyber threats necessitates a proactive method towards securing delicate information. Leveraging cloud solutions offers an engaging solution for organizations seeking to fortify their information security steps. By entrusting credible cloud company with information monitoring, organizations can use a wealth of protective features and cutting-edge technologies that bolster their defenses against malicious actors. The question emerges: exactly how can the usage of cloud solutions change information safety and security techniques and give a durable guard versus possible susceptabilities?
Significance of Cloud Security
Making sure durable cloud security procedures is critical in safeguarding delicate information in today's digital landscape. As organizations significantly count on cloud solutions to store and refine their data, the requirement for solid safety and security methods can not be overstated. A violation in cloud safety and security can have serious repercussions, ranging from economic losses to reputational damages.
One of the main factors why cloud protection is important is the shared obligation design employed by a lot of cloud service suppliers. While the supplier is liable for securing the infrastructure, customers are responsible for safeguarding their data within the cloud. This department of duties emphasizes the significance of implementing robust security procedures at the individual level.
Furthermore, with the expansion of cyber hazards targeting cloud environments, such as ransomware and data violations, companies should stay proactive and alert in mitigating threats. This entails regularly updating safety protocols, monitoring for dubious tasks, and informing employees on finest practices for cloud safety. By prioritizing cloud protection, companies can better safeguard their sensitive information and promote the count on of their stakeholders and consumers.
Data Encryption in the Cloud
Security in the cloud typically includes the usage of cryptographic formulas to scramble data into unreadable layouts. This encrypted data can just be figured out with the equivalent decryption key, which adds an extra layer of safety. Additionally, several cloud service carriers offer file encryption systems to safeguard data at remainder and en route, enhancing general data defense. Executing robust file encryption techniques together with other safety actions can substantially bolster a company's defense against cyber threats and safeguard important info stored in the cloud.
Secure Information Backup Solutions
Data back-up options play a critical duty in guaranteeing the durability and protection of visit here data in case of unexpected incidents or information loss. Secure information backup services are important parts of a durable information safety and security strategy. By consistently backing up data to safeguard cloud servers, companies can alleviate the dangers connected with information loss as a result of cyber-attacks, hardware failures, or human mistake.
Implementing safe and secure information backup options involves picking trusted cloud solution providers that use file encryption, redundancy, and data honesty actions. Furthermore, data stability checks make sure that the backed-up data stays tamper-proof and unchanged.
Organizations should develop automated backup routines to make sure that information is consistently and efficiently supported without hand-operated treatment. Regular testing of information repair processes is additionally essential to ensure the efficiency of the back-up remedies in recouping information when needed. By spending in secure information backup options, services can improve their information safety and security position and decrease the effect of potential information violations or disruptions.
Role of Gain Access To Controls
Implementing rigid access controls is crucial for preserving the protection and stability of delicate info within organizational systems. Gain access to controls act as a critical layer of protection against unapproved gain access to, making sure that just informative post authorized people can watch or control sensitive information. By defining that can access specific resources, companies can restrict the danger of information violations and unapproved disclosures.
Consistently upgrading and examining accessibility controls is essential to adjust to business modifications and progressing safety risks. Continuous surveillance and auditing of access logs can aid detect any suspicious tasks and unauthorized accessibility efforts without delay. In general, robust gain access to controls are fundamental in guarding delicate details and mitigating safety and security threats within organizational systems.
Conformity and Laws
Regularly making sure compliance with relevant regulations and criteria is vital for companies to support information security and personal privacy measures. In the world of cloud services, where information is frequently stored and processed on the surface, adherence to industry-specific regulations such as GDPR, HIPAA, or PCI DSS is essential. These policies mandate details data managing methods to safeguard delicate information and make sure user personal privacy. Failure to follow these laws can cause serious fines, including fines and lawsuits, damaging an organization's online reputation and trust fund.
Several service providers offer security capacities, access controls, and audit trails to help organizations meet information protection requirements. By leveraging compliant cloud solutions, organizations can boost their data security position while fulfilling regulative obligations.
Verdict
Finally, leveraging cloud solutions for enhanced information safety and security is vital for organizations to protect sensitive information from unapproved accessibility and prospective breaches. By carrying out robust cloud security procedures, consisting of data security, secure back-up solutions, gain access to controls, and conformity with regulations, services can benefit from sophisticated protection steps and knowledge supplied by cloud provider. This aids reduce dangers properly and guarantees the privacy, honesty, and availability of data.
Information back-up options play a vital he said role in ensuring the durability and safety and security of data in the event of unforeseen incidents or information loss. By regularly backing up information to safeguard cloud servers, companies can reduce the dangers linked with information loss due to cyber-attacks, equipment failures, or human mistake.
Carrying out safe and secure information backup solutions involves choosing dependable cloud solution suppliers that offer security, redundancy, and information integrity actions. By spending in safe and secure data backup remedies, organizations can boost their data security pose and minimize the influence of prospective data violations or disruptions.
Report this page